Marvelous Tips About How To Check For Sql Injection

Sql injection (sqli) is one of the most common attacks in cyberspace.
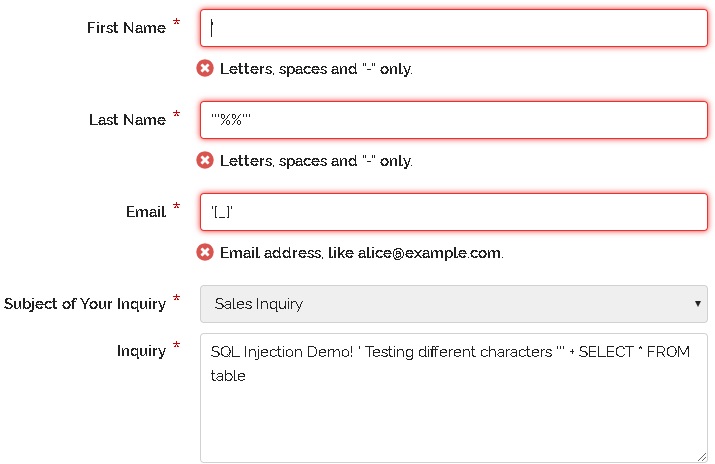
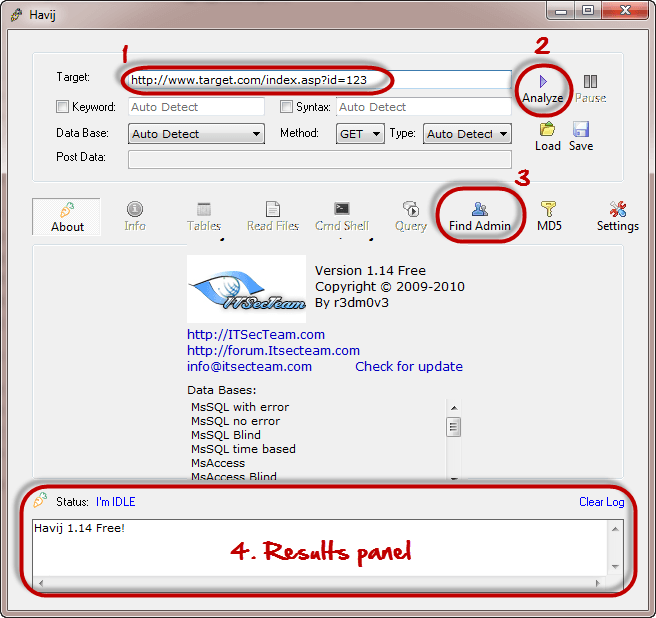
How to check for sql injection. The first step towards achieving a successful sql injection attack is to detect vulnerabilities. So firstly, we have to enter the web url that we want. 2 bedroom houses for rent in albany georgia;
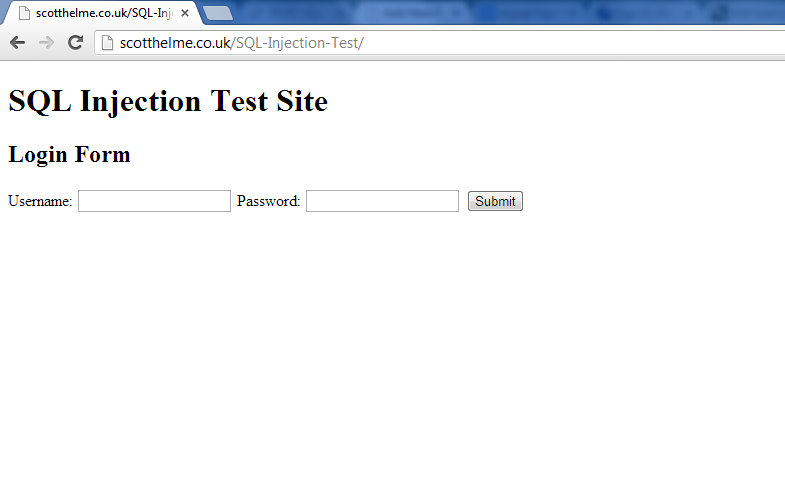
Most web applications and frameworks revolve around these same principles, building out forms to manipulate the underlying data which is stored in the database. Can that person spot a sql injection bug in your code? Sql injection (sqli) refers to an injection attack wherein an attacker can execute malicious.
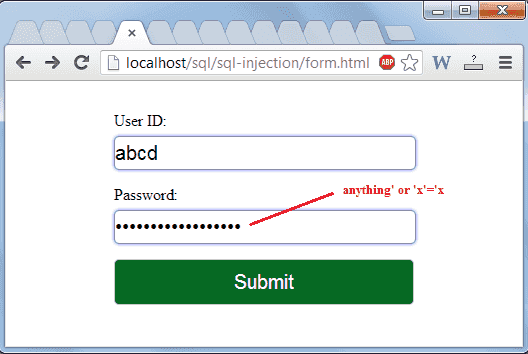
If there is nothing to prevent a user from entering wrong input, the user can enter some smart input like this: Personalized gifts for someone who lost a loved one; Standard sql injection testing classic sql injection.
You use sql commands to create, read, update and delete (crud) the information inside of your tables. Let’s look at the four types of sql injections. Then, the sql statement will look like this:
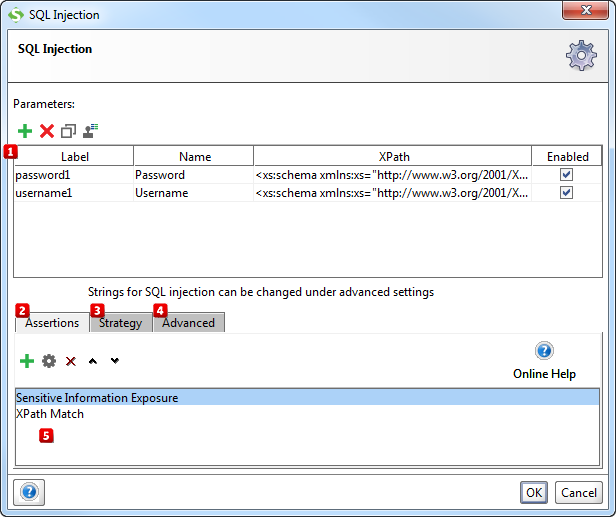
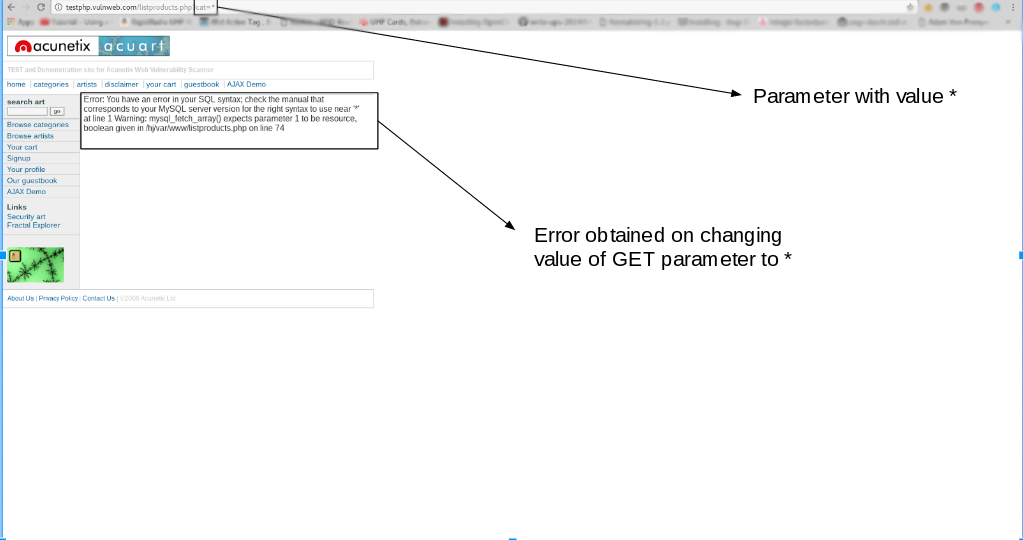
Query reshaping or redirection (above) error message based (no such user/password) blind injections; Getting unauthorized access to the system using sql injection. For testing sql injection in these kind of urls, we just use our payloads as before, but after the parameter :
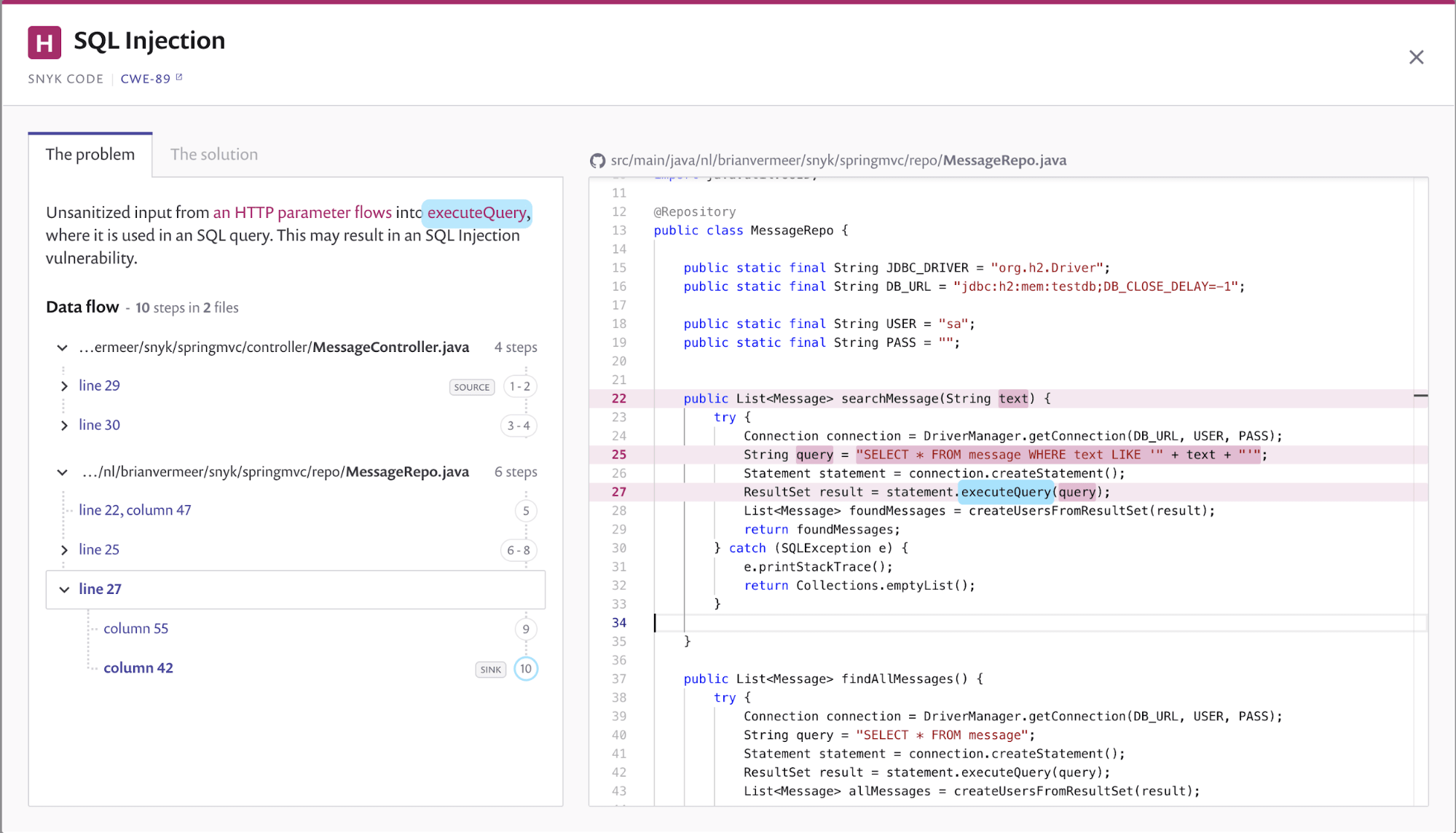
Select id, firstname, lastname from authors. Select * from users where username='$username' and password='$password' a similar query is. The following script shows a simple sql injection.